|
|
【上次團務會議】
日期:111年11月1日(二)
時間:下午 1:30-3:00
地點:板橋國小
公文與附件:
團務報告:
研究與探討:
新北市資訊科技教材設計分工:
- 三年級:劉嘉嘉、陳怡仲、蔡家丞
- 四年級:許智豪、吳家儀
- 五年級:邱昭士、詹博文
- 六年級:羅英財、郭書軒
分享與交流:
日期:111年11月1日(二)
時間:9:00-12:00
地點:新北市教育研究發展中心2F電腦教室(大觀國中校內)
主題:影音整合控制器與Mirroring 360
講師:捷達講師
公文與附件:
課程講義:
【上次社群活動】
日期:111年10月28日(五)
時間: 12:10開始用餐,12:40開始主題分享
地點:二年16班教室
主題:與腦相容學習理論與應用
講師:陳堯方老師
活動報告:
- 備有熱飲、蔬食午餐、水果、點心,請自備環保杯及餐具唷~
投影片:
大腦與認知科學-YouTube
網路資源:
- 基於腦科學的教學該如何進行?
- 與腦相容的教學原則與策略初探
- 作者:林瑜一
- 本文的目的在探討與腦相容的教學原則,與探究與腦相容的教學策略。
- 採文獻內容分析法,蒐集學者對於與腦相容教學原則的論述,歸納相關概念得到「十二個與腦相容的教學原則」。接著,再蒐集學者專家對教師如何將與腦相容的教學方法應用在教學實務的各種文字描述,進一步以上述十二個原則為概念架構,歸納出「四十個與腦相容的教學策略」。
- 本文所歸納的與腦相容教學原則有:
(1)學習是生理/物理的
(2)覺知能力與經驗間是相互影響的
(3)大腦天生會藉由組型尋求意義
(4)情緒是學習成功的關鍵
(5)大腦是同時處理部份和整體的(概念)
(6)注意力是波動的
(7)學習伴隨著認知和非認知的歷程
(8)至少有兩種不同取徑的記憶形式,可透過不同的技巧來增進記憶
(9)低壓力高挑戰可促進學習
(10)每一個人的大腦都具有其獨特性
(11)正向的感覺有助於學習
(12)大腦期待多元的輸入,學習整合了全身的感官覺知。
這十二個原則及相對應的教學策略應可幫助教師對與腦相容教學的了解,並更易應用於教學實務提升教學效能。
- 「與腦相容的教學原則與策略初探」部份內文下載
學員回饋:
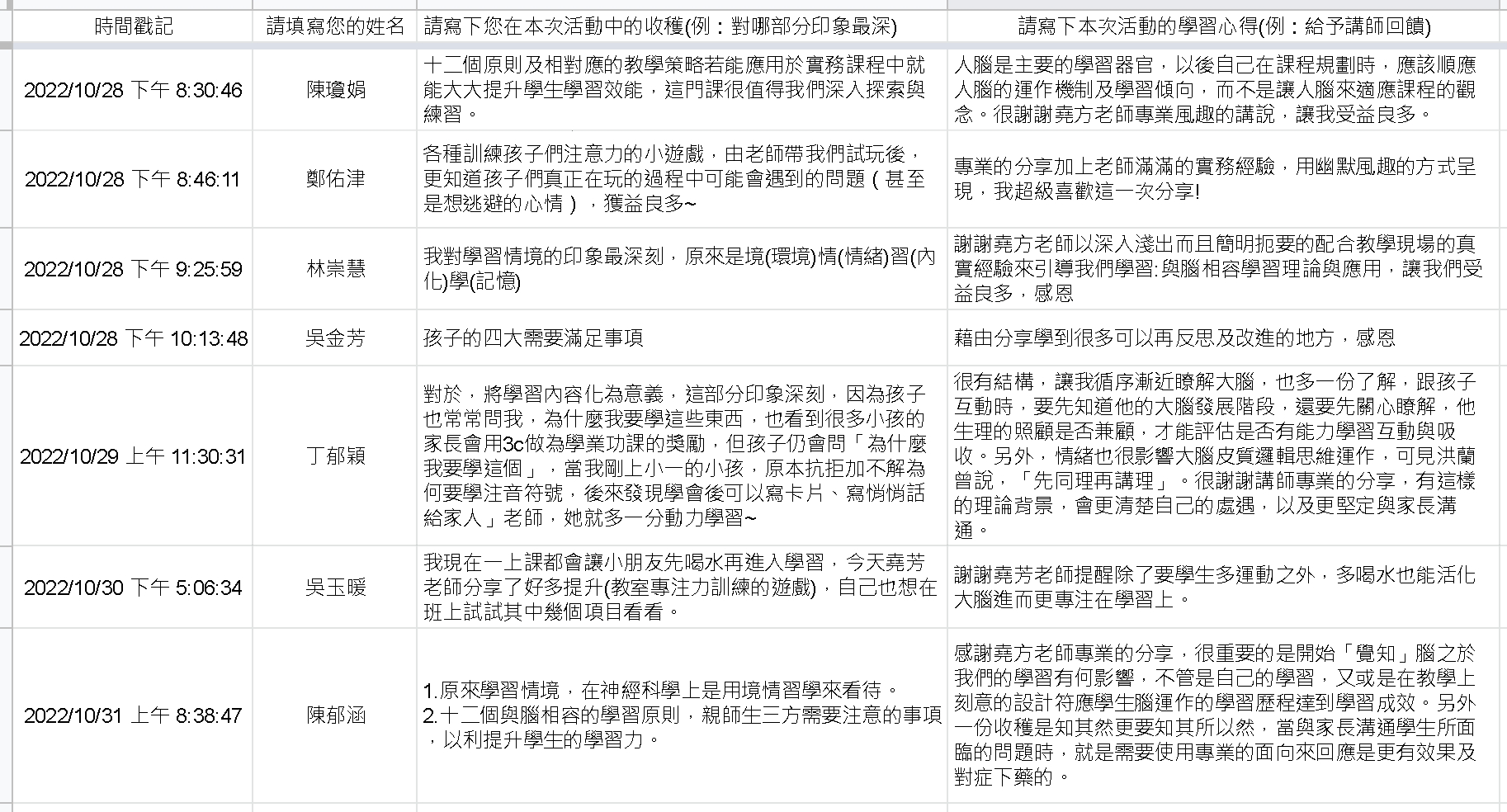
活動照片:
日期:111年10月26日(三)
時間:13:30-16:30
地點:雲端教室
主題:教案甄選說明會暨數位學習教學模式設計研習(PBL教學模式設計)
講師:教資科何春緣輔導員
公文與附件:
徵選活動:
- 本市111年度數位學習創新教案徵選活動預計11月1日至11月30日報名,12月進行評選,預計明(112)年1月初公告評選結果,並於1月至2月辦理頒獎典禮。
講義:
110年教案徵選教案分享:
自主學習組:
PBL學習組:
補充教材:
相關連結:
|
|












































